What is Phishing Attacks & How it is done?
Phishing is a type of cyber attack that involves tricking individuals into disclosing sensitive information, such as passwords or financial information. This is typically done through fake emails or websites that look like they are from a legitimate source.
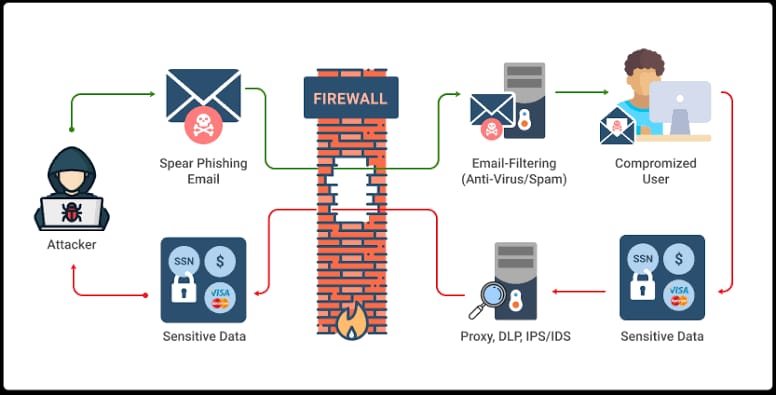
The attacker may send an email posing as a reputable organization, such as a bank or government agency, and request that the recipient provide sensitive information. The email may contain a link that, when clicked, takes the recipient to a fake website designed to steal the information.
Phishing attacks can be difficult to detect, as the attackers often go to great lengths to make their emails and websites look legitimate. However, there are steps that individuals can take to protect themselves, such as being cautious of emails that ask for sensitive information and verifying the authenticity of emails and websites before entering any information.
It's also important for organizations, including movie post-production companies, to educate their employees about phishing attacks and to implement security measures, such as anti-phishing software, to help prevent these attacks.
Process:
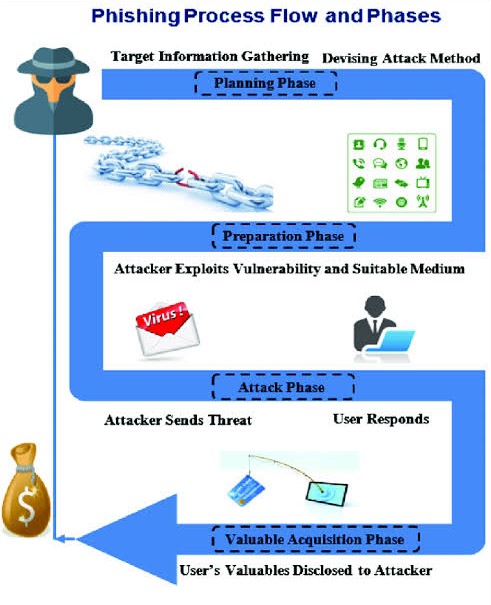
The process of a phishing attack can typically be broken down into the following five steps:
1. Research: The attacker researches their target, gathering information such as the target's name, email address, and the organizations they are affiliated with.
2. Setup: The attacker creates a fake email or website that looks like it is from a legitimate source, such as a bank or government agency.
3. Delivery: The attacker sends the fake email or links to the fake website to their target.
4. Trickery: The target is tricked into disclosing sensitive information, such as passwords or financial information, by following a link in the fake email or entering information on the fake website.
5. Exploitation: The attacker uses the sensitive information to gain unauthorized access to the target's accounts or to steal sensitive data. This information can then be used for financial gain or to cause harm to the target.
It's important to be vigilant and cautious when receiving emails or visiting websites, especially when they request sensitive information. Being aware of these five steps can help individuals recognize a phishing attack and take steps to protect themselves.
Awareness on Phishing scams for Post-production
- Understanding ransomware
- Regular data backups.
- Disaster recovery plan
- Employee education
- Strong passwords
- Network security
Case Study :-
One real-world example of a phishing attack in the movie post-production industry took place in 2018. In this case, attackers targeted a post-production company working on a high-budget film. The attackers sent a phishing email to an employee, posing as a trusted vendor and requesting the employee to click on a link and provide their login credentials.
Unknowingly, the employee entered their login credentials, which gave the attackers access to the company's internal systems. The attackers then gained access to sensitive information, including the rough cut of the film, and demanded a ransom in exchange for not releasing the stolen data.
The post-production company was forced to pay the ransom to get the stolen data back, causing a significant financial loss and damage to their reputation. This case highlights the importance of educating employees on how to recognize and avoid phishing attacks, as well as having proper security measures in place to protect sensitive information.