
What is SQL Injection & How it is done?
SQL injection is a type of security vulnerability that occurs in web applications that use Structured Query Language (SQL) to interact with a database. The vulnerability allows an attacker to inject malicious SQL code into a web application's input fields, allowing them to manipulate the database in various ways, such as extracting sensitive data or modifying its contents.
SQL injection attacks are often carried out by submitting malicious input into web forms or by crafting URLs that contain malicious SQL code. When the web application processes this input, it may execute the malicious SQL code and compromise the security of the underlying database.
To prevent SQL injection attacks, it is important to validate user input, sanitize it to remove any malicious characters, and use parameterized queries instead of concatenating user input directly into SQL statements. Additionally, web developers should be familiar with the security features provided by their database management systems and use them to secure their databases.
Process :
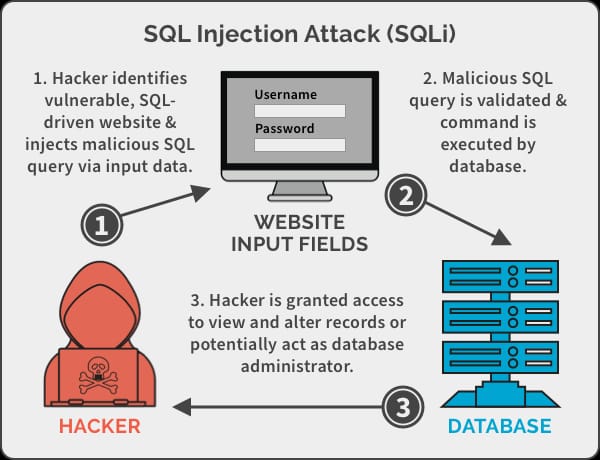
SQL injection attacks occur when a web application does not properly validate or sanitize user input before using it in SQL statements that interact with a database. The attacker can exploit this vulnerability by injecting malicious SQL code into the input fields of the web application. The following is a general overview of the process of an SQL injection attack:
1.Identification: The attacker identifies a vulnerable web application that uses SQL to interact with a database.
2.Input Tampering: The attacker manipulates the input fields of the web application to include malicious SQL code.
3.Execution: The web application processes the malicious input and executes the injected SQL code.
4.Data Retrieval: The attacker can use the executed SQL code to retrieve sensitive data from the database, such as passwords, credit card numbers, or personal information.
5.Data Modification: The attacker can also use the executed SQL code to modify the contents of the database, such as altering or deleting records.
6.Command Execution: In some cases, the attacker can also use SQL injection to execute arbitrary commands on the underlying system, potentially compromising the security of the entire server.
It is important to note that SQL injection attacks can have serious consequences, including theft of sensitive information, disruption of services, and financial loss. To prevent these attacks, web developers should properly validate and sanitize user input and use parameterized queries to interact with databases.
Awareness on SQL Injection for Post-production
- Input validation
- Parameteized Queies
- Escaping Special Characters
- Stored Procedure
- Least Privilege
- Regular Updates
- Monitoring
- Security Awareness
Case Study :-
One real-world example of an SQL injection attack on a post-production company is the attack on Sonic DVD. In 2007, Sonic DVD, a leading producer of DVD software, suffered a major data breach as a result of an SQL injection attack. The attacker was able to inject malicious SQL code into the company's web application, gaining access to sensitive information such as customer names, addresses, credit card numbers, and more.
The attack had a significant impact on Sonic DVD and its customers. The company had to spend a considerable amount of time and resources to investigate the breach, secure its systems, and inform affected customers. Many of its customers had their personal and financial information compromised, leading to identity theft and financial losses.
This attack highlights the importance of properly securing web applications and databases to prevent SQL injection attacks. By implementing best practices such as input validation, parameterized queries, and regular security updates, organizations can reduce the risk of these attacks and protect their sensitive information.